In the ever-evolving landscape of the digital world, cyberattacks continue to pose significant threats to individuals, organizations, and governments alike. As technology advances, so do the tactics of cybercriminals. The Acronis Cyberthreats Report for the second half of 2023 sheds light on cyberthreats and trends that dominated the cybersecurity landscape during this period. Here are key insights from the report.
Cyberthreat trends in H2 2023
1. Ransomware Gang Activity: In 2023, ransomware continued to be a major threat to large and medium-sized businesses, including government, health care and other critical organizations. LockBit, CI0P, BlackCat/ALPHV, Play, and 8Base were the most active, with LockBit topping the list with 1,000 victims.
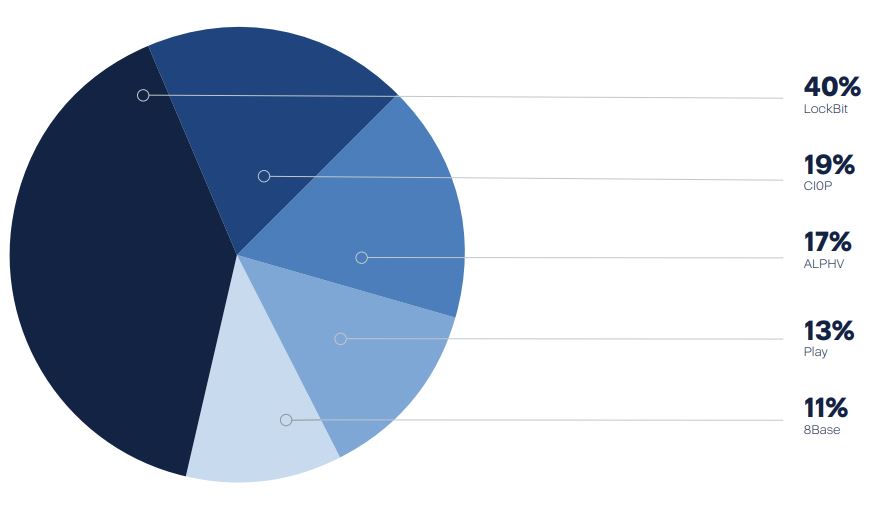

Notably, BlackCat/ALPHV, a prominent player in 2022, maintained its position by infecting a considerable number of high-profile victims.
2. Attacks on Managed Service Providers (MSPs): The report highlights the relentless attacks on Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs). As crucial allies in providing robust IT infrastructure and cybersecurity, MSPs have become attractive targets for cybercriminals as breaching an MSP’s network can potentially grant access to sensitive data from multiple organizations, making them a one-stop-shop for cybercriminals.
3. Escalation of Phishing and Malicious Emails: Phishing and malicious emails continue to be primary vectors of infection, with a 222% increase in email-based attacks in H2 2023 compared to the second half of 2022.
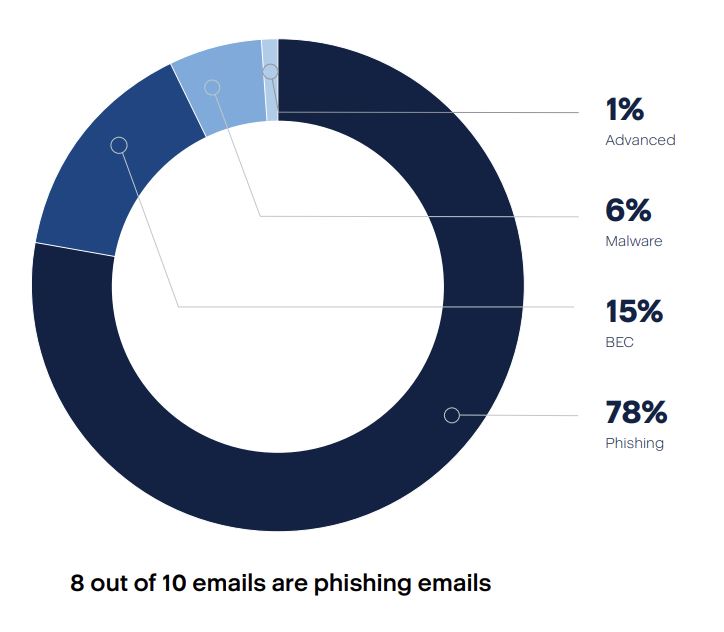

4. Dominance of Data Breaches: Significant data breaches persistently marred the cybersecurity landscape in 2023, affecting various sectors. Data breaches, often associated with ransomware attacks, took different forms, including silent exfiltration during attacks, resulting in data leaks on the dark web or underground forums. Information stealers played a significant role in both large and small incidents observed in the second half of 2023.
5. Rise of AI-Powered Threats: The adoption of machine learning and AI by cybercriminals led to highly sophisticated attack methodologies. AI-driven threats, including spear phishing, AI-generated social engineering attacks, deepfake technology, adaptable malware, and AI-powered botnets, challenge organizations to rethink their security strategies.
Cyberthreats prediction for 2024
The Acronis report foresees several concerning threat trends for the year ahead, including:
1. AI-driven phishing attacks: Acronis anticipates a surge in phishing attacks leveraging generative AI, creating highly realistic fake messages and scenarios to deceive users into disclosing sensitive information.
2. Phishing beyond email: Traditional email phishing will evolve onto communication platforms like Microsoft Teams, catching users off guard. The trend of QR code-based phishing and stealing web session tokens to bypass MFA authentication is expected to persist.
3. Deepfake exploitation: AI-generated deepfakes will become prevalent tools for cybercriminals, manipulating individuals or public opinion through hyper-realistic fake videos and audio recordings. These deepfakes are particularly on the rise in business email compromise (BEC) scams and extortion threats.
4. Attacks on AI models: While cybercriminals will increasingly target AI models, the current high costs of such attacks outweigh the benefits for the majority. The proliferation of techniques listed on the MITRE ATLAS matrix indicates a growing array of methods, including stealing API keys for resale or increasing operational costs by forcing AI systems to overwork.
5. Automated cyberattacks: AI’s role will extend beyond enhancing attack sophistication, contributing to a surge in volume and frequency. Acronis expects automated cyberattacks to become more prevalent, enabling attackers to strike multiple targets simultaneously with minimal effort. This will necessitate AI vs. AI scenarios, demanding automated defense systems to react promptly and mitigate the attacks.
6. Disabling security solutions: The persistence of trends like “bring your own vulnerable driver” will continue to target security solutions directly, with attackers aiming to disable EDR systems to carry out undetected malicious activities. The simple uninstallation of solutions may go unnoticed by IT departments.
7. Identity provider and MFA bypasses: Multifactor authentication (MFA) and centralized identity providers will be prime targets for attackers seeking access to a wide array of resources. The prediction includes an uptick in the use of phishing-resistant MFA combined with Zero Trust Architecture (ZTA) solutions.
8. Human errors due to complexity and stress: The rising complexity of IT systems and stress on individuals managing them will lead to an increase in human errors. Despite the availability of AI copilots mitigating the skills gap, integrating diverse data sources correctly remains challenging, leaving potential openings for cyberattacks.
9. Living off your infrastructure: Attackers will increasingly employ ‘living off the land’ strategies, exploiting legitimate tools and services of MSPs or executing supply chain attacks to access multiple targets through a single breach.
Acronis recommendations for cybersecurity
Password Security:
- Ensure strong, private passwords for enhanced security.
- Avoid sharing passwords and utilize password manager software.
- Use long, unique passwords for every service to thwart brute force attacks.
- Encourage the use of multifactor authentication for added protection.
- Lock laptops and desktops, even during remote work, to prevent unauthorized access.
Patch OS and Apps:
- Stay vigilant about software vulnerabilities to mitigate potential risks.
- Promptly install updates for operating systems like Windows.
- Enable auto-updates for popular software vendors such as Adobe.
- Timely patching is crucial to address vulnerabilities that could be exploited by cyber threats.
Phishing Preparedness:
- Remain cautious and refrain from clicking on suspicious links.
- Recognize that malicious links can emerge from various sources, including instant messenger apps, emails, and forum posts.
- Leverage dedicated URL filtering functionality, as offered by Acronis Cyber Protect Cloud, to enhance protection against phishing attempts.
- Remain vigilant against the constant influx of new phishing messages and malicious websites.
Source
Read next: 3.5 million Indian travelers affected in massive data breach via passports, mobile numbers and emails!
The post Email-based attacks increase 222% in H2 2023 from H2 2022, finds Acronis Cyberthreats report appeared first on Daily Host News.









