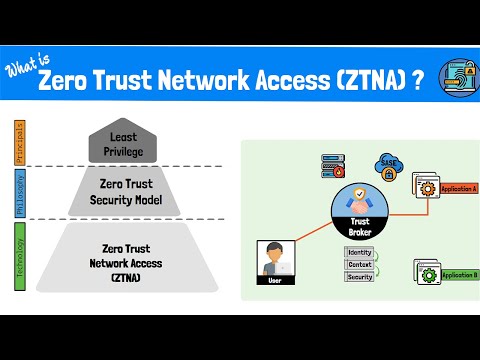
This video provides an in-depth examination of Zero Trust Network Access (ZTNA), a technology that, on the basis of the Zero Trust security concept, enables safe remote access with little risk. To begin, it provides an explanation of the Zero Trust paradigm, highlighting the fact that no user or device, regardless of whether it is internal or external, should be trusted immediately. A comprehensive verification process that includes identity checks, contextual knowledge, and security posture evaluation is required in order to earn trusting relationships.
The presenter provides an overview of the role that ZTNA plays in the implementation of the Zero Trust principles, concentrating on the ways in which it varies from standard virtual private networks (VPNs) by giving access to apps on a need-to-know basis rather than providing users with wide network access. The trust broker, which is a crucial component of ZTNA, is described, and it is explained how it functions as an intermediary that validates and continuously checks the credentials of users who are seeking access to services.
For the purpose of demonstrating how ZTNA may be implemented using either cloud-based services or on-premises equipment, practical examples and vendor solutions are provided. Finally, a real-world example is shown that illustrates how a user accesses a business application by using ZTNA. This scenario serves to demonstrate the continuous verification process at hand.